Issue: You would like to require (or attempt) TLS encryption on inbound email communications from specific partner email domains.
Solution Snippet: In this walkthrough we will be creating a partner Sender Group and Mail a Flow Policy that prefers or requires TLS encrypted communication.
Solution Walkthrough
Create a new Mail Flow Policy called “TLS_Required_Policy”
click Mail Policies > Mail Flow Policies
click the Add Policy button
put TLS_Required_Policy in the Name field
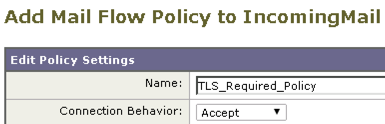 Scroll down to Security Features and change the TLS setting to “Required“.
Scroll down to Security Features and change the TLS setting to “Required“.
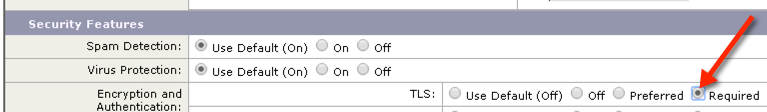
click the Submit button to save the new Mail Flow Policy.
Next we will create a new Sender Group which will contain the ‘TLS required’ entities that send email to your organization:
click Mail Policies > HAT Overview
click “Add Sender Group” button
Name the Sender Group “TLS_Required_Group”
Select the “TLS_Required_Policy” from the Policy drop down menu
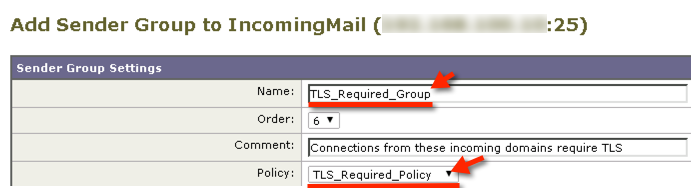 click the “Submit and Add Senders” button
click the “Submit and Add Senders” button
Add the IP and/or hostnames in the ‘Sender’ field and click Submit:
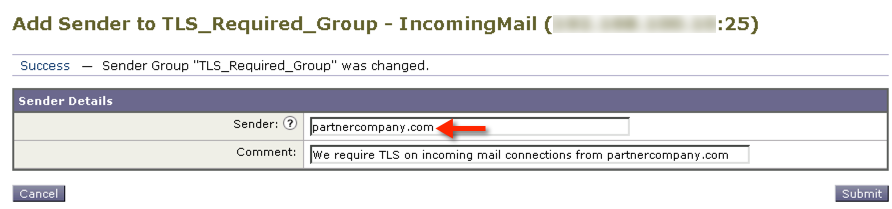 Note: I’ve found that the sending mail servers IP or Hostname is what is what the IronPort uses, which may not be the same as the senders email domain name. You may need to review the headers on the incoming mail to determine the sending mail server hostname or IP.
Note: I’ve found that the sending mail servers IP or Hostname is what is what the IronPort uses, which may not be the same as the senders email domain name. You may need to review the headers on the incoming mail to determine the sending mail server hostname or IP.
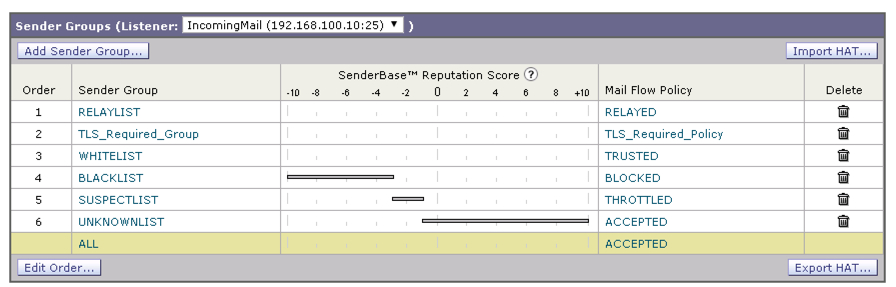
Position the “TLS_Required_Group” Sender Group above the Whitelist Sender Group:
click Mail Policies > HAT Overview
click ‘Edit Order’ button
change the arrangement so that TLS_Required_Group is placed above the WHITELIST group
Note: you can alternatively substitute “TLS_Preferred” in the group/policy names and select TLS Preferred rather than Required in the settings. TLS preferred will attempt TLS, and if TLS cannot be established will receive mail as clear text.
In order to test, contact the organization you setup to receive TLS email from and ask them to send you some test emails. Next, open the Monitor menu page to verify incoming IronPort TLS.
Here are steps to setup TLS for outbound mail or enable TLS on all incoming email.
question.
why does the new sender group need to be positioned in between “relay list” and “whitelist” ?
is there a particular reason?
Hi Navishkar, I believe the new TLS_Required sender group needs to go above Whitelist is because the groups are parsed in an iterative fashion, meaning it uses the policy of the first group that the sender is matched with. If Whitelist was above TLS_Required then a sender being in the whitelist would have the whitelist policy applied and then TLS would not be required because it hit the Whitelist group/policy first since it was the first match. Let me know if this makes sense or you have any questions. If you find Cisco ESA documentation to the contrary please let me know that as well. Thx
hi there
thanks for the great article.
Great Article. Thank you!