Issue: After completing the steps to install a new SSL certificate on your Cisco IronPort ESA you need to assign the certificate to the various Cisco IronPort functions that require encryption (email communications, TLS, Quarantine and admin web pages).
Activating the new SSL Certificate:
-
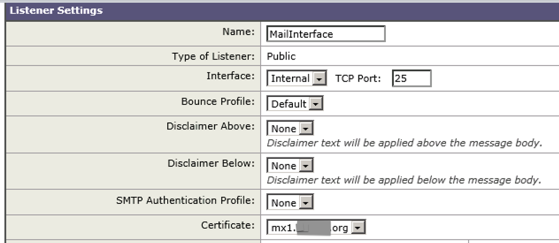
To assign the new certificate for inbound SMTP email communication, open Network > Listeners and select the new certificate
-
Assign the certificate for use in Outbound TLS based email communications:
Mail Policies > Destination Controls > Global Settings > Edit Global Settings > click the Certificate drop down and select your new Certificate.
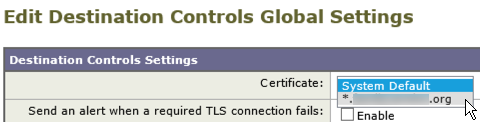
Note: Specifying a certificate under destination controls tells the IronPort ESA which cert to use *if* TLS is enabled on outbound communications. In other words, specifying the cert in the drop down will not actually enable TLS on the IronPort. Follow these steps to enable TLS on the IronPort ESA.
Next: assign your new certificate to the Cisco IronPort ESA quarantine and admin web pages
Is it possible to have two different inbound SSL/Cipher settings for TLS? One one hand, I need to disable TLSv1 for a particular inbound domain of ours. However, disabling TLSv1 globally seems to result in a lot of errors that say “454 TLS not available due to a temporary reason”
Hi Mark, I haven’t attempted this myself. It may be worth taking up with support. Please do post the solution if your figure it out. Sorry I don’t have an answer on this.
Hi there! I have a problem authenticating on the ESA appliance with the domain username. It is weird as the other ESA can authenticate over LDAP very fine. They both are in a cluster and ldap configuration is done over there.
Can you tell me possible reasons for NOT authenticating me on the esa2 but just fine on esa1? From cli i can ping the ldap server just fine…
“I can show you where to set the Cisco ESA certs for web administration and quarantine.”
Is this done with the CLI? I already have a wildcard cert installed on the IronPort but I don’t see anywhere in the GUI (version 8.3.6) where to apply it to HTTPS (or Spam Quarantine)
Thanks!
How to use your third party SSL cert for HTTPS (ESA quarantine page and web admin page): https://enterpriseit.co/ironport/assign-certificate-quarantine-admin/
Let me know if you have any questions
You do not specify how to apply the cert for the Quarantine web interface for users. Or does setting the Secure Connection to SSL automatically use the installed SSL cert?
My apologies, I’m missing the screenshots and don’t have access to an IronPort at the moment. If you’d like to do a join.me I can show you where to set the Cisco ESA certs for web administration and quarantine.
UPDATE: Here are the steps to specify your cert for HTTPS (IronPort quarantine and web admin pages): https://enterpriseit.co/ironport/assign-certificate-quarantine-admin/